Introduction
“… the very spark that marks us as a species … our tool-making, our ability to bend [nature] to our will … also give us the capacity for unmatched destruction.”—Barack Obama [1]
The twentieth century evidenced the increasing use of state-of-the-art science and technology (S&T) in warfare. Included in this S&T armamentarium were new chemical and biological agents that could be yoked to extant forms of S&T (e.g., aircraft, ordnance, etc.) to facilitate delivery in kinetic engagements [2]. Such changes in the instruments of warfare served as impetus for formulating international signatory treaties and conventions (e.g., The Chemical Weapons Convention [CWC] and Biological Toxins and Weapons Convention [BTWC]) to govern these agents’ development and use [3]. However, recent advancements and interdisciplinary convergence in chemical, biological, data, computational, and engineering fields have enabled creation of chem-bio agents that are not (currently) regulated by these governances and, when taken together, can establish significant deterrent leverage in nonkinetic and kinetic domains [4, 5].
The 5 D’s of Deterrence
Deterrence involves insight, planning, development of structural and functional resources, engagement of personnel and services, and use of methods and tools aimed at influencing (in multidirectional ways) the intent and activities of individual and collective others. In the main, deterrence entails and obtains five essential domains of effect (i.e., the 5 D’s of Deterrence), which are not mutually exclusive and can and arguably should be interactive, complimentary, and reciprocal in both articulation and effect as follows:
Definition of those enterprises and efforts that can be identified as representative foci (i.e., targets) for deterrent influence. The nature and extent of these targets are important to terminating the directionality of deterrence, i.e., by suppressing certain elements, factors, endeavors, and effects and/or fortifying others to shape the trajectory and valence of desired outcomes.
Detection of those burdens, risks, and threats that constitute relevant fields and forces that are to be defined, identified, and targeted. Detection of the targetable elements should include both quantitative and qualitative descriptive metrics and qualitative metrics that describe what, why, and how certain factors pose burden, risk, and threat requiring deterrent intervention. Quantitative metrics provide evidentiary support for the currency and extent of burden, risk, and threat incurred.
Determination of required tactics and strategies of deterrent engagement. Such methods are aimed at qualifying and quantifying required resources, services, and personnel necessary to maintain a defensible status quo vs. those variables necessary to induce and enable protracted directional change. In both cases, calculation of gains and losses incurred by omission of deterrent intervention, as well as commission of deterrent intervention, can and should be incorporated into the overall relative cost projections of fiscal, temporal, personnel expenditures, and losses.
Disruption of relative status quo to induce and sustain deterrent action and effect upon identified targets. Disruption is directional, and the trajectory of disruptive intent and plotting of effects should focus upon the valent goal(s), as well as possible off-goal effects that could occur because of disruptive drift and/or postdisruptive reaction by the targeted source. It is important to recognize and plot as best possible those disruptive effects incurred by deterrent intervention in the short term (within 2 to 12 months), intermediate term (13–36 months), delayed (37–60 months), and possible long-term (60–120 months) manifestations. Modeling and forecasting deterrent and disruptive effects beyond the 120-month horizon have become difficult, if not impossible, in certain cases because of (1) fractal diffusion of applied deterrent interventions and effects and (2) multifactorial reaction and response patterns (both by the target of deterrence and affiliated allied and/or interactive entities within the dynamic system affected) [5].
Diminution of risk and threat, either by eliminating or revising threat sources and resources, or by instituting countering resources and variables that redirect laws, intentions, activities, and outcomes of the identified target focus. Diminution of threat can be (1) mitigative (i.e., decreasing existing burdens and risks that pose current or future term threat) or (2) preventive (i.e., proactively impeding activities that can and likely will pose risk and/or threat). In both instances, such diminution can involve destructive and disruptive (i.e., restructuring) elements and activities to eliminate or reestablish constructs, conditions, and contexts of effect within the target and its zone(s) of operational influence.
Dimensions of Deterrent Effect(s)
Deterrence methods can be engaged proactively, reactively, nonkinetically, or kinetically based upon exigencies, contingencies, and particular allowances and constraints of the engagement space and (geo-socio-political) environment.
Proactive deterrence seeks to provide means and methods that exert influential force upon identified targeted burdens, risks, and threat resources to suppress, if not eliminate, current and ongoing development of force strengths and capabilities that have been identified as posing current and/or near-term problems and/or danger to the deterring agents (and/or the stability and security of an identified system/environment).
Reactive deterrence is directed activity against an identified clear and present burden, risk, or threat to mitigate the extent of negative impact, redirect current and near-term manifestations, and/or influence current and future conduct of same or similar activities; it can reduce the relative calculus of burden, risk, and/or incurred threat.
Nonkinetic deterrence involves influence operations to include soft weapons (of economics, policy, law, and/or ecological and environmental influence) to leverage relative power in ways relevant to exercising hegemonic control.
Kinetic deterrence involves the use of military and intelligence force, characteristically by the actual employment of methods and tools (i.e., as weapons) of disruption and/or destruction in accordance with defined parameters of hostile activity (in either defensive or offensive postures).
Chem-Bioscience and Technology in/for Deterrence Operations: Effects and Vectors
During the 20th century, chemical and biological agents have emerged as viable elements in national deterrence initiatives. Various chemicals, toxins, and microbes (e.g., sarin, ricin, and anthrax) have been considered as tools for political and military deterrence. The potential for chemical and bioterrorism via the use of such agents by states and nonstate actors poses significant challenges to current and near-term global security [6, 7].
Chemical and biological deterrence obtains the following three primary dimensional effects:
- Fear factor – The primary aim of using chemical and biological agents for deterrence is to instill fear in adversaries. The threat of chemical or biological attacks can make opponents reframe intentions and actions considering (real or perceived) burdens, risks, and threats induced by nonkinetic or kinetic use of such implements. Additionally, fear(s) that a competitor or adversary has such agents can influence narratives, attitudes, and actions about the relative viability and value of existing treaties and signatory conventions aimed at governing their development and use and, in ways, foster implicit or explicit brinksmanship in this space.
- Ambiguity and uncertainty – The mere possession of these agents, or ambiguous statements regarding their potential use, can create uncertainty and deter competitors and potential adversaries. The fear of a recognized or unknown chemical/biological threat can significantly influence decision-making processes—and resultant political, economic, and military postures—of opposing parties.
- Economic (e.g., low cost and high impact) – Chemical and biological agents can be relatively inexpensive to produce and deploy compared to more “conventional” weapons. Their potential to cause widespread disruptive effects with plausibly destructive (ripple) manifestations and limited investment (i.e., “costs”) and considerable impact (i.e., “gain) makes them attractive tools for nonkinetic or kinetic (pro- and/or reactive) deterrence [8–10].
These effects can be employed and leveraged in and across several engagement vectors and settings, which include the following:
Nations’ dual-use research projects and programs – The dual-use nature of many nations’ chemical/biological research enterprises, which can have benevolent biomedical and more “grey zone” if not explicitly disruptive (and manifestly destructive) effects, complicates international efforts to satisfactorily surveille, assess, and govern their development and use [11, 12]. Such dual-use research of concern (DURC), while defined by extant multinational conventions, remains somewhat problematic to evaluate given (1) categorical limitations of those research directions and products currently identified as potentially problematic and of concern, (2) growing progress in gene editing and synthetic biologic methods that could render currently “innocuous” substances and agents as pathogenic and disruptive, and (3) the architecture(s) and activities of competitor nations’ industrial/commercial efforts that remain veiled and thus shielded by corporate proprietary interests and protections [13, 14].
Development and use by nonstate actors – An increasing number of nonstate actors are active in this Chem-Bio and Data and Cyberscientific and Technological (CB-DCST) space either as independent entities or designated proxies for nation-states’ operations [10]. Nonstate actors can acquire chemical/biological capabilities via (1) acquisition of nation state-developed tools and products, (2) provision/acquisition of nation states’ methods for developing and deploying such agents, and/or (3) specifically dedicated efforts of research, development, and utilization of these agents. These variables further complexify international efforts at oversight and deterrence (of such groups’ operations) while concomitantly fortifying their collectives’ deterrence capabilities [15].
Verifying nations’ and nonstate actor groups’ compliance with international treaties and conventions regarding chemical and biological agents (e.g., BTWC, CWC, Declarations of Helsinki, EU Exportation Regulations, etc.) presents challenges of oversight and enforcement. Access to accurate intelligence is crucial to assessing iterative developments in chem-bio S&T (CBST) that pose current risk and potential threats and effectively deterring their use [16]. However, relatively seamless infrastructures and functions of trans-Pacific and Atlantic peer competitor nations’ “triple helix” of government, academic research, and commercial/industrial enterprises, as fortified by their national legal parameters, makes direct insight to potential DURC difficult and fosters impediments to “deep surveillance”—absent what would constitute apparent violations of internationally recognized intellectual property law(s) [17, 18].
In light of such gaps in regulatory oversight and governance, and as evidenced by the COVID crisis, there is a real risk of accidental release of chem-bio agents leading to unintended consequences and significant disruption of public health, national stability, and biosecurity, with proximate and more distal destructive effects in a variety of dimensions (e.g., economic, social, political, military) and on a range of scales (e.g., organizational, institutional, local, regional, national, and global) [19–23]. This risk underscores the importance of and need for deterrence postures to mitigate or prevent such trajectories of probable and possible effect, which could be intentionally or unintentionally incurred by competitor groups’ activities in this space.
The use of chemical and biological agents for political and military deterrence operations is a complex and contentious issue which remains a serious concern for reasons of (1) ongoing enterprises in this space by peer-competitor, proxy nations, and nonstate actors; (2) the relative facility of research and development (R&D) capabilities facilitated by current innovations in gene editing, synthetic biology, and reciprocal engagement of data/cyber S&T; and (3) relative opacity of extant (international) policy, treaties, and laws of oversight, surveillance, regulation, and governance. Thus, the potential—if not probability—for such methods, tools, and products to be employed and leveraged in nonkinetic and/or kinetic deterrence operations is clear and present and hence poses demonstrable risk and threat(s) to U.S. and allied biosecurity and biodefense. This risk and threat become forever viable given the capabilities conferred by using data and computational S&T in ways that fortify and augment research, development, and use applications and venues of chem-bio methods and agents.
Data and Cybersciences and Technology: Machine Learning (ML) and Artificial Intelligence (AI)
As previously noted [24, 25], big data and cyberscientific and technological tools and methods (e.g., ML and iterations of AI) are force multipliers for research, development, and use of various types of CBST. Ongoing progress in neurocognitive S&T has facilitated further development of ML/AI via innovations in neuromorphic computing systems’ design and construction [26, 27]. As shown in Figure 1, this has created an “operationalizable omnibus” of S&T wherein impacts are generated by the constituent parts as fortified by a de-siloed, force-multiplied approach to R&D and utility in practice (i.e., a mereoform typology) and the entirety (i.e., a holoform typology)—as a combinatory entity (CB-DCST).
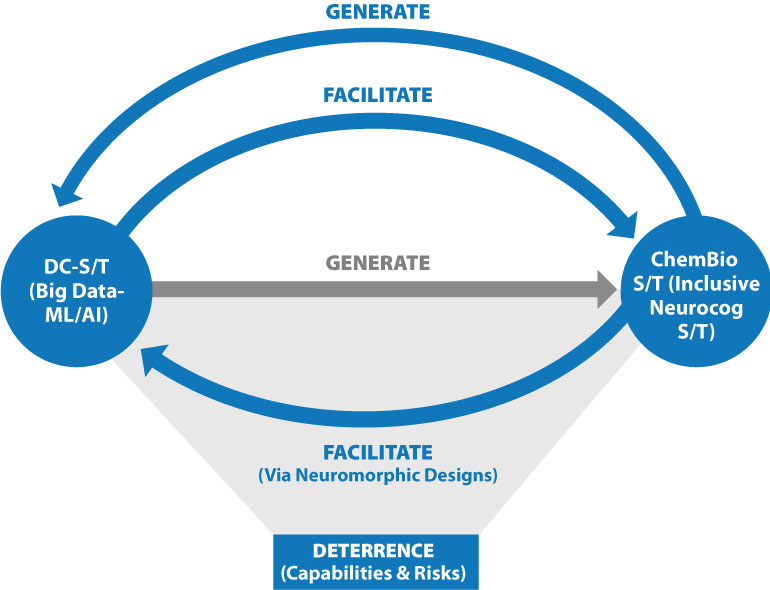
Figure 1. Diagram of the Interaction(s) and Reciprocity of Force Multiplication of Big Data, Cyber, and CBST (Source: J. Giordano).
The military domain has witnessed significant advancements and applications of DCST-powered systems inclusive of data and ML/AI-optimized analytics (if/when coupled to aforementioned tools and methods of CBST) to develop “precision pathologies” capable of maximally disruptive effects on targeted individuals and/or groups and the development (and increasing use) of weaponry with varying degrees of human-dependent and governed independence and autonomy [28]. The iterative superiority and deployment of such DCST-driven capabilities can exert significant deterrent influence over peer-competitor/potential adversarial nations’ nonkinetic and/or kinetic engagement and activities in this space (see Figure 2). In the figure, the interactive domains and dimensions of DC/CBST, when taken individually or in combination, can be utilized in (1) nonkinetic (“soft weapon”) influence/deterrent operations to affect economics, biopsychosocial narratives, sentiments, and actions of targeted individuals and groups (engaging and influencing social and physical ecologies on various scales and levels) and (2) kinetic (“hard weapon”) operations, in which disruption characteristically involves/incurs more destructive effect(s) by using information, cyber- and/or chem-bio warfare. (Note that DCST and/or CBST can be used nonkinetically and/or kinetically in covert, clandestine, overt, or combinatory ways.)

Figure 2. Diagram of Interactive DCST and CBST Domains and Dimensions (Source: J. Giordano).
Toward Preparedness
Considering ongoing developments in CB-DCST, it is both reasonable and realistic to presume and acknowledge that current (radical levelling) and emergent methods and tools can and will be employed for deterrence initiatives and operations on the 21st century global stage. Furthermore, the multinational engagement of scientific and technological research establishes a basis for many states to exercise capabilities in this sphere. Current efforts in the CB-DCST spaces have been described in a series of advisory reports from the National Research Council commissioned by the United States Army and Defense Intelligence Agency during the early part of the 21st century [29, 30]. These reports offered recommendations for the military intelligence communities to identify and pursue CB-DCST for operational use. Subsequent reports, including several white papers of the Strategic Multilayer Assessment Branch of the Joint Staff, Pentagon have acknowledged that CB-DCST has high potential for present operational use in a variety of security, intelligence, and defense deterrent enterprises [31–34].
Of note is the imposing possibility to incur deterrence through “changing minds and hearts” by altering the will or capacity to fight and/or idiosyncratic and collective cognitive, emotional, and behavioral domains using singular or combined use of CB-DCST tools and methods [35]. Such applications and effects include, but would not be limited to, the following:
- Modifying cognitive constructs and resultant emotions and behaviors,
- Mitigating aggression and directing or influencing cognitions and emotions of affiliation or passivity,
- Incurring disruptive effects (e.g., resource paucity and resultant burden of lifestyle) and directly incurring morbidity and/or disability; in these ways, neutralizing competitors’ and/or potential opponents’ capacities in multiple domains of social and international engagement, and
- Inducing indirect or direct destructive effects, (against infrastructures, resources, various functions, and mortal effects against humans, agricultural stocks, etc.).
It is important to recognize that even nonkinetic engagement of deterrence means and methods can be provocative, if not contentious, as these may be regarded as elements and activities of biopower [36]. In this light, it is opined that when attempting to balance benefits, burdens, risks, and harms of deterrence operations in the context of nonkinetic, preemptive, and preventative activity (defensible under a construct of justification to prevent war, i.e., jus contra bellum), as well as kinetically (within operational parameters of just war theory, i.e., jus ad bello/jus in bellum), any such methods and outcomes will need to be considered compared to those produced by more traditional means, inclusive of policy and warfare (with the latter entailing consideration of past and present availability and use of existing armaments like explosive, radiological, and nuclear devices and emergent developments in CB-DCST) [37].
Given multinational enterprises in CB-DCST, it is naive to think that the same trends that compelled the development and use of these tools for disruptive and deterrent influence will be impeded merely by considerations of (1) burdens and risks that might arise as S&T advances ever farther into frontiers of the unknown, (2) potential harms that such advances could intentionally or unintentionally occur, and (3) ethical legal and sociopolitical issues instantiated by positive and negative effects of implications of S&T advances for deterrent aims and ends. Thus, a simple precautionary principle in which risk benefit ratios determine the trajectory and pace of scientific and technological advancement is not tenable on an international level. This is because there is real possibility—if not probability—that competitive nations and/or insurgent groups could fund and clandestinely, if not covertly, conduct research, development, test, and evaluation (RDT&E) of such S&T beyond the auspices and influences of the United States and its allies’ guidelines and policies.
Instead, a process that entails some measure of precaution together with significant preparedness will be required [38, 39]. Such preparedness mandates knowledge of what technological accomplishments can be achieved given incentives and resources currently available and afforded; whether such work is being prepared and/or conducted; what groups are involved in such efforts; overt and/or covert intentions and purposes of these activities; possible scenarios, effects, and consequences that could arise from various levels of scientific and technological progress and their use; and what (deterrent) measures can and should be taken to counter risks and threats posed by such progress and its effects [40, 41]. For this approach to work, surveillance is necessary, although international oversight and governance of novel CB-DCST RDT&E may be difficult. What can be governed and regulated are those ways in which these aspects of S&T efforts are conducted in and employed by U.S. agencies in conjunction and cooperation with international (political, economic, and military) allies.
Consideration of Ethico-Legal and Social Issues
Ethical questions need to be pragmatically posed and prudently addressed in balance with the interests of the public (i.e., national) security and protection, as well as key elements of global standing and global power [42, 43]. CB-DCST can and will be engaged to evoke outcomes relevant to national security, intelligence, and defense operations by countries and nonstate entities to achieve goals that may be contrary to the public welfare interests of the United States and its allies. As history has shown, a dismissive posture that fails to recognize and acknowledge the reality of these risks and threats increases the probability of susceptibility to possible, if not probable, harm in an open society.
In an open society, it is the responsibility of government to protect the polis [44]. This will necessitate efforts to establish proactive defensive knowledge of those S&T capabilities and the vulnerabilities that they exploit to recognize how CB-DCST could be used to leverage deterrent power and develop stances in readiness and response to such realities. A meaningful stance of preparedness requires rigorous analysis and addressing of the technical and ethical, legal, and social issues that the use, nonuse, or misuse of CB-DCST generate. Guidelines and policies must be informed and formulated by realistic appraisal and addressing of each and all these issues consistent with core precepts of other international deliberations upon using various S&T implements in deterrent military and intelligence operations. Such consideration would need to evaluate those ways that S&T should or should not be studied, developed, and employed. Key questions include whether the use of certain CB-DCST approaches incurs greater or lesser risks and harms than other methods of deterrent operations and if—and what—limits should be applied to any possible development and use of such S&T in current and near-term deterrence initiatives [45].
Conclusions
The development and employment of CB-DCST in agendas of influence and deterrence are a certainty on the 21st century global stage. Undoubtedly, such S&T can influence the norms and conduct of multinational interactions, competition, and conflict. The future engagement space will depend not only upon achieving S&T dominance but of establishing national and international resources necessary to exercise intelligence surveillance, oversight, and engagement of discourse and dialectic toward establishing international policy and law.
Currently, the development and use of such S&T are somewhat underregulated and not included in dual-use export safeguards, thus making effective oversight of potential dual-use research of concern difficult. This combination of “blank slate” and “unknown terrain” dimensions creates additional difficulties in realistic biosecurity forecasting and preparedness. It is important to acknowledge that the rapidity of advances in these fields often outpaces securitization. Thus, efforts to more accurately define, detect, and direct deterrent capabilities of CB-DCST can and should be rightly viewed as a clear and present exigency.
References
- Obama, B. “The Memory of the Morning of August 6, 1945, Must Never Fade.” NY Times, CLVX: no. 57246; p. 82016, 8 March 1996.
- Stockholm International Peace Research Institute (SIPRI). “The Problem of Chemical and Biological Warfare.” Vol. 1: The Rise of CB-Warfare, Stockholm: Almqvist and Wiksell, 1971.
- Stockholm International Peace Research Institute (SIPRI). “The Problem of Chemical and Biological Warfare.” Vol. 3: CBW and the Law of War, Stockholm: Almqvist and Wiksell, 1971.
- Gerstein, D., and J. Giordano. “Re-Thinking the Biological and Toxin Weapons Convention?” Health Security, vol. 15, no. 6, pp. 1–4, 2017.
- DeFranco, J. P., M. Rhemann, and J. Giordano. “The Emerging Neurobioeconomy: Implications for National Security.” Health Security, vol. 18, no. 4, pp. 66–80, 2020.
- Snow, J. J., and J. Giordano. “Aerosolized Nanobots: Parsing Fact From Fiction for Health Security – A Dialectical View.” Health Security, vol. 17, no. 1, pp. 74–76, 2019.
- Snow, J. J., and J. Giordano. “Public Safety and National Security Implications of the Horsepox Study.” Health Security, vol. 16, no. 2, pp. 1–3, 2018.
- Dando, M. R. “Neuroscience and the Problem of Dual Use.” Cham. CH: Springer, 2020.
- Dando, M. R., M. Crowley, M. R. Dando, and L. Shang (editors). Preventing Chemical Weapons: Arms Control and Disarmament as the Sciences Converge. London: Royal Society of Chemistry, 2018.
- Dando, M. R. Neuroscience and the Future of Chemical-Biological Weapons. Basingstoke: Palgrave-Macmillan, 2015.
- Dando, M. R. “Biologists Caught Napping While Their Work Militarized.” Nature, vol. 460, p. 933, 2009.
- Dando, M. R. “The Impact of Modern Biology and Medicine on the Evolution of Offensive Biological Warfare Programs in the Twentieth Century.” Defense Analysis, vol. 15, no. 1, pp. 43–62, 1999.
- DiEuliis, D., and J. Giordano. “Why Gene Editors Like CRISPR/CAS May Be a Game-Changer for Neuroweapons.” Health Security, vol. 15, no. 3, pp. 296–302, 2017.
- Chen, C., J. Andriola, and J. Giordano. “Biotechnology, Commercial Veiling, and Implications for Strategic Latency: The Exemplar of Neuroscience and Neurotechnology Research and Development in China.” In Strategic Latency: Red, White, and Blue: Managing the National and International Security Consequences of Disruptive Technology, Livermore CA: Lawrence Livermore Press, pp. 12–32, edited by Z. S. Davis and M. Nacht, 2018.
- Giordano, J. “The Neuroweapons Threat.” Bull. Atomic Sci., vol. 72, no. 3, pp. 1–4, 2016.
- Giordano, J. “Battlescape Brain: Engaging Neuroscience in Defense Operations.” HDIAC Currents, vol. 3, no. 4, pp. 13–16, 2017.
- De Franco, J. P., and J. Giordano. “Mapping the Past, Present, and Future of Brain Research to Navigate the Directions, Dangers, and Discourses of Dual-Use.” EC Neurol., vol. 12, no. 1, pp. 1–6, 2020.
- Etzkowitz, H. The Triple Helix: University-Industry-Government Innovation in Action. NY: Routledge, 2008.
- Wurzman, R. “Inter-Disciplinarity and Constructs for STEM Education: At the Edge of the Rabbit Hole.” Synesis: Journal of Science Technology Ethics and Policy, vol. 1, pp. 32–35, 2010.
- Venkatram, V., D. DiEuliis, and J. Giordano. “The COVID Crisis: Implications and Lessons for United States’—and Global—Biosecurity.” In COVID-19: Analysing the Threat, New Delhi: Pentagon Press, pp. 397–405, edited by A. Lele and K. Roy, 2020.
- DiEuliis, D., N. B. Kohls, and J. Giordano. “Of Nemesis and Narcissus: Lessons COVID May Provide for Enterprises—and Ethics—of Global Health Promotions and Biosecurity.” In Medicine and Ethics in Times of Corona, Zürich: LIT Verlag, pp. 323–329, edited by M. Woesler and H. M. Sass, 2020.
- DiEuliis, D., and J. Giordano. “COVID-19: Lessons to Be Learned for Biosecurity and Future Operational Environments.” J. Def. Res. Engineer., vol. 8, no. 3, 2020.
- DiEuliis, D., and J. Giordano. “The Need for Modernization of Biosecurity in the Post-COVID World.” mSphere, vol. 12, pp. 8–14, 2022.
- DiEuliis, D., and J. Giordano. “Regarding and Reducing Risks of the Biotechnology Revolution.” NCT J., vol. 6, pp. 2–6, June 2022.
- DiEuliis, D, and J. Giordano. “Neurotechnological Convergence and ‘Big Data:’ A Force-Multiplier Toward Advancing Neuroscience.” In Ethical Reasoning in Big Data, pp. 71–80, April 2016.
- Collmann, J. Ethical Reasoning in Big Data: An Exploratory Analysis. NY: Springer, edited by S. A. Matei, 2016.
- Giordano, J. “Integrative Convergence in Neuroscience: Trajectories, Problems and the Need for a Progressive Neurobioethics.” In Technological Innovation in Sensing and Detecting Chemical, Biological, Radiological, Nuclear Threats and Ecological Terrorism, (NATO Science for Peace and Security Series), NY: Springer, edited by A. Vaseashta, E. Braman, and P. Sussman, 2012.
- Shook, J. R., T. Solymosi, and J. Giordano. “Ethical Constraints and Contexts of Artificial Intelligence in Biomedical Applications for Public Health and Safety, National Security, and Defense Operations.” In Artificial Intelligence and Global Security. Future Trends, Threats and Considerations, London: Emerald, pp. 137–152, edited by Y. Masakowski, 2020.
- DiEuliis, D., and J. Giordano. “Precision Medicine and National Security: Implications, Issues and Imperatives.” Mil. Med., vol. 17, no. 12, pp. 35–39, 2021.
- National Research Council of the National Academy of Sciences (NAS). Emerging Cognitive Neuroscience and Related Technologies. Washington D.C.: National Academies Press, 2008.
- National Academies of Sciences, Engineering, and Medicine (NASSEM). Biodefense in the Age of Synthetic Biology. Washington, D.C.: National Academies Press, 2018.
- Giordano, J. (editor). “Topics in the Neurobiology of Aggression: Implications for Deterrence.” U.S. DoD; Strategic Multilayer Assessment Group – Joint Staff/J-3, 2013.
- Giordano, J. “Intersections of “Big Data,” Neuroscience and National Security: Technical Issues and Derivative Concerns.” In A New Information Paradigm? From Genes to “Big Data,” and Instagrams to Persistent Surveillance: Implications for National Security, pp. 46–48, U.S. DoD, Strategic Multilayer Assessment Group – Joint Staff/J-3/Pentagon Strategic Studies Group, edited by H. Cabayan et al., 2014.
- Giordano, J. (editor). “Leveraging Neuroscience and Neurotechnological (NeuroS/T) Development With Focus on Influence and Deterrence in a Networked World.” U.S. DoD, Strategic Multilayer Assessment Group – Joint Staff/J-3, 2014.
- Giordano, J., J. P. DeFranco, and L. R. Bremseth. “Radical Leveling and Emerging Technologies as Tools of non-Kinetic Disruption.” U.S. DoD, Strategic Multilayer Assessment Group – Joint Staff/J-3/Pentagon Strategic Studies Group, 2021.
- Giordano, J., and R. Wurzman. “Neurotechnology as Weapons in National Intelligence and Defense.” Synesis J. Sci. Technol. Ethics Policy, vol. 2, pp. 138–151, 2011.
- Bremseth, L. R., and J. Giordano. “What COVID-19 and China’s Grand Strategy May Teach About a History of the Future.” In Strategic Latency Unleashed: The Role of Technology in a Revisionist Global Order, Livermore CA: Lawrence Livermore Press, pp. 109–120, edited by Z. S. Davis, F. Gac, C. Rager, P. Reiner, and J. Snow, 2021.
- Tennison, M., J. Giordano, and J. Moreno. “Security Threat Versus Aggregated Truths: Ethical Issues in the Use of Neuroscience and Neurotechnology for National Security.” In Neuroethics: Anticipating the Future, Oxford: Oxford University Press, pp. 531–553, edited by J. Illes and S. Hossein, 2017.
- Giordano, J., C. Forsythe, and J. Olds. “Neuroscience, Neurotechnology and National Security: The Need for Preparedness and an Ethics of Responsible Action.” AJOB-Neurosci., vol. 1, no. 2, pp. 1–3, 2010.
- DeFranco, J. P., D. DiEuliis, L. R. Bremseth, J. J. Snow, and J. Giordano. “Emerging Technologies for Disruptive Effects in Non-Kinetic Engagements.” HDIAC Currents, vol. 6, no. 2, pp. 49–54, 2019.
- Tractenberg, R. E., K. T. FitzGerald, and J. Giordano. “Engaging Neuroethical Issues Generated by the Use of Neurotechnology in National Security and Defense: Toward Process, Methods, and Paradigm.” In Neurotechnology and National Security and Defense: Practical Considerations, Neuroethical Concerns. Boca Raton: CRC Press, pp. 259–278, edited by J. Giordano, 2015.
- Giordano, J. “Neurotechnology, Global Relations, and National Security: Shifting Contexts and Neuroethical Demands.” In Neurotechnology and National Security and Defense: Practical Considerations, Neuroethical Concerns. Boca Raton: CRC Press, pp. 1–10, edited by J. Giordano, 2015.
- Casebeer, W. D. “A Neuroscience and National Security Normative Framework for the Twenty-First Century.” In Neurotechnology and National Security and Defense: Practical Considerations, Neuroethical Concerns, Boca Raton: CRC Press, edited by J. Giordano, pp. 279–284, 2015.
- Johnson, J. T. Morality and Contemporary Warfare. New Haven: Yale University Press, 1999.
- Bower, R., and J. Giordano. “Use of Neuroscience and Neurotechnology in Interrogations: Practical Considerations and Neuroethical Concepts.” AJOB Neurosci. Suppl., vol. 3, p. 3, 2012.
Biography
James Giordano is a Pellegrino Center professor of neurology and biochemistry, chief of the Neuroethics Studies Program, and director of the Program in Biosciences, Biosecurity and Ethics of the Cyber SMART Center at Georgetown University Medical Center; senior bioethicist of the Defense Medical Ethics Center; and Stockdale distinguished fellow of science, technology, and ethics at the U.S. Naval Academy. He currently serves as a nonresident senior fellow of the Simon Center for the Professional Military Ethic, U.S. Military Academy at West Point, NY. Dr. Giordano holds a BSc in physiological psychology from St. Peter’s College; an M.S. in neuropsychology from Norwich University; an MPhil in philosophy of science and Ph.D. in biopsychology, both from the City University of New York; and has completed post-doctoral fellowship training in neurotoxicology and pathology at the Johns Hopkins University Schools of Medicine and Public Health.


