Introduction
Over the winter of 1990–1991, military leaders in Washington, D.C., identified a new threat to the security of U.S. armed forces deployed around the globe—pizza, i.e., delivery pizza. An enterprising local pizzeria owner noticed that his late-night delivery orders to Central Intelligence Agency Headquarters would spike immediately before an international conflict or to the Pentagon whenever the U.S. Department of Defense (DoD) was preparing to execute a major troop movement [1, 2]. He was also not keeping it confidential. As a result, reporters from Time and The Washington Post, eager for a byline on the imminent start of the Persian Gulf War, traded mention of his pizzerias’ offerings for information. One prominent cable news host reportedly concluded that from then on, the “bottom line” for national security journalists was clear: “always monitor the pizzas” [3].
Whether the story of the “Pentagon Pizza Index” was ever truly a useful means of predicting the deployment of American forces is somewhat irrelevant. Rather, for DoD leadership, the Pizza Index came to symbolize the dawn of a new era of warfare—one dominated by the pervasive use of digital communication devices and constant presence of live, real-time global media streams [4, 5]. The challenges posed by this new “Information Age” in the 1990s demanded an organized and concerted response from strategic thinkers within the DoD. They answered, in part, by developing new military doctrine—the fundamental principles, ideas, methods, and practices that guide the use of force. New doctrinal concepts and field manuals for both “Information Warfare” and “Information Operations” soon emerged [4].
Since the 1990s, the DoD and the service branches alike have repeatedly reviewed, codified, and revisited what constitutes information and what role it might play in the future of combat [4–6]. By the late 2010s, this perennial cycle of revision began anew. The doctrinal concepts and manuals on applying “informational power” or working in the cognitive realm had become a mere afterthought to the military planning process—they were either overly broad in scope or had been written to such a level of specificity that they were all but indistinguishable from the technologies that enabled them [4, 6].
In the last five years, however, information doctrine has seen a renaissance within the DoD, and the U.S. Army has largely led the way. As the Joint Force’s largest component, and given its remit for land operations, the Army is central to the DoD’s strategic focus on preparing for the possibility of conventional, large-scale combat operations (LSCOs) against a peer threat. It is within this backdrop that the U.S. Army promulgated Army Doctrine Publication (ADP) 3-13, Information [7], in late 2023. This publication guides soldiers on how to best think about the military use of information and gives detailed direction on how to exploit it to build and apply combat power. It also introduced an important new phrase to the lexicon—information advantage (IA). Its definition is deceptively simple: IA is “the use, protection, and exploitation of information to achieve objectives more effectively than enemies and adversaries do” [7].
Overview
This article explores the IA concept as it functions within the U.S. Army’s broader operational concept—multidomain operations (MDOs). It explores the ways in which threat actors might, at the outset of an LSCO-sized conflict, use nonkinetic and antiaccess information-based attacks to disrupt, hinder, and degrade U.S. efforts to generate and deploy expeditionary military force from the homeland—a strategy sometimes referred to as “preclusion” (see Figure 1). This is a critical area of study because adversaries now possess powerful and effective cyberspace, media, and psychological stand-off capabilities that threaten the Joint Force’s freedom of action at the very outset of a military engagement.
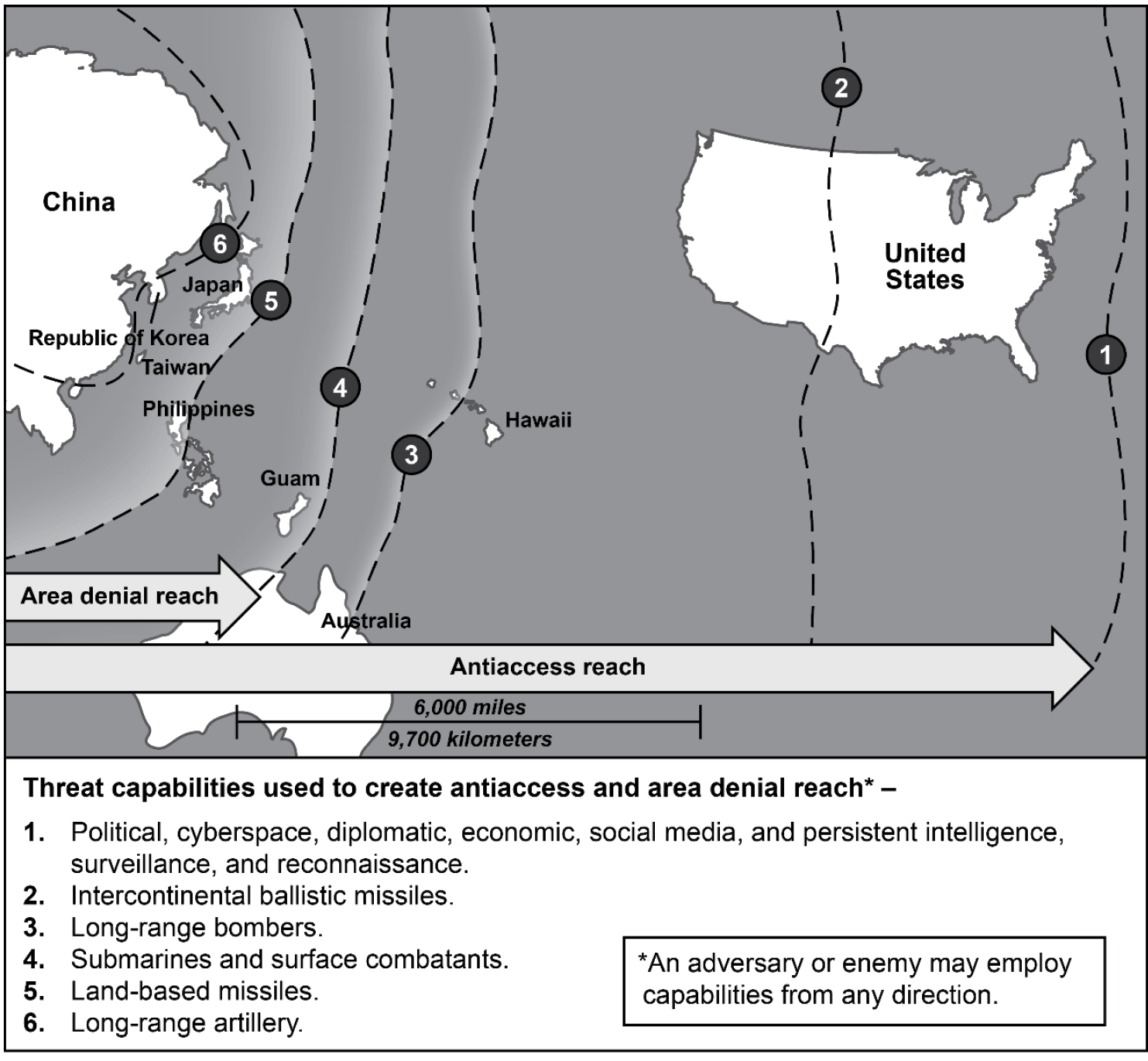
Figure 1. Notional Example of Threat Adversary Preclusion of U.S. Force Projection Using NonLethal, NonKinetic Informational Means (1) to Isolate and Demoralize the United States, Kindle Civic Instability, and Manipulate Public Opinion (Source: U.S. Army [10]).
In the future fight, U.S. forces will have to “fight for, defend, and fight with information” even before a conflict escalates into a kinetic battle [7]. This coming challenge is further complicated by the fact that American force projection operations from the homeland have never been truly contested by adversary forces. U.S. military leadership now sees the contestation of future deployments as all but inevitable, and such attacks are expected to come primarily from the information dimension. As DoD strategic documents routinely point out, the defense of traditional power projection capabilities from nonkinetic cyber and informational effects may well be the deciding factor in determining who will prevail [8, 9].
This article proceeds in three parts. First, it traces how U.S. Army doctrine and practice have considered the role of information (especially computerized knowledge-management systems) during deployment exercises in the 1970s–1980s and how they enabled the “spectacular” success of projecting U.S. forces into Saudi Arabia during the Persian Gulf War. For military planners, these events underscored the fact that the DoD’s ability to mass and deploy forces is underpinned by its information-based communication and logistics systems, many of which were seen as either inadequate or insecure.
Second, the article presents a review of the MDO operational concept’s core and traces how the information dimension functions within and across its domains in U.S. Army doctrine. It notes that the task of achieving and preserving IA emerged as a counter to the nonkinetic cyber and information-based threats developed by peer states since the 1990s. Recognizing that future adversary actions will target public and private media to offer false narratives, it also highlights the centrality to the IA concept of subjective perception.
Third, three avenues are explored through which threat actors might seek to generate harmful cognitive effects in service members and the public to preclude U.S. force projection. As a recounting of a fictionalized digital attack on a deploying soldier’s family helps illustrate, adversaries will conduct persistent reconnaissance and intelligence on soldiers and their loved ones to gain advantages; they will exploit DoD and other information systems to directly influence soldier action; and they will interfere with the public to hinder or degrade U.S. Army force projection activities.
Force Projection at the Start of the Information Age
As military historians and active-duty generals point out, the U.S. Army undergoes a major transformation roughly every 40 years [10, 11]. Its most recent overhaul began in the 1970s, partly because of Gen. Donn A. Starry, a four-star armored cavalry commander who took the reins of the U.S. Army Training and Doctrine Command (TRADOC) in 1977. Starry arrived to find TRADOC in a phase of considerable transition. Although U.S. involvement in Southeast Asia was then in the rearview mirror, the easing of tensions in American-Soviet relations (known as détente) had begun to deteriorate, and the threat of Soviet antiarmor weapons loomed large [12]. Starry played an outsized role in rethinking the Army’s warfighting framework, known as “AirLand Battle.” By the mid-1980s, its tactics had been reformed to contend with the nonlinear battlefields of the future—ones marked by using long-range reconnaissance technologies and complex, computerized command and control (C2) systems [12, 13].
Command Post Exercise (CPX) “Nifty Nugget”
Starry’s emphasis on the role of C2 in enabling rapid maneuver and force sustainment was an apt one, for the general was familiar with the baleful consequences of subpar C2 capabilities [14]. In 1978, the DoD convened a massive, 21-day-long CPX that simulated a full-scale, whole-of-government effort to project U.S. military force into the European theater (see Figure 2) [15, 16]. CPX Nifty Nugget aimed to stress-test the Pentagon’s force generation and mobilization plans, military-civilian coordination at the federal level, and the DoD’s logistical information technology (IT) systems—and stress was just about all that Nifty Nugget uncovered. The DoD was unable to “locate” ~350,000 of the ~800,000 fictional troops that the scenario called for, and exercise participants “could not even agree on the meaning of the word ‘mobilization’ ” [15, 17].
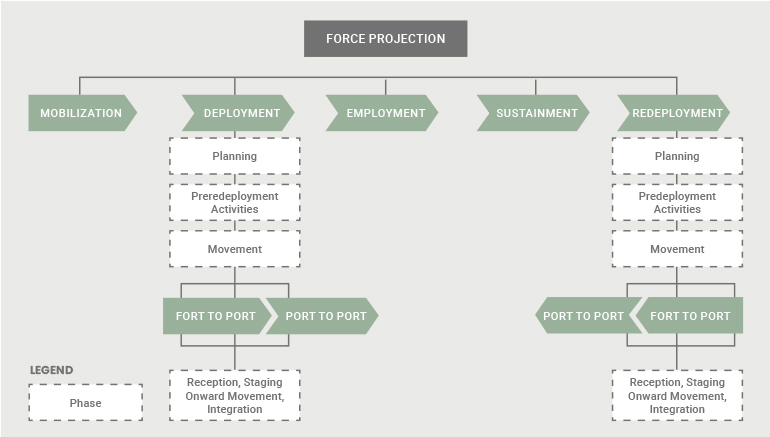
Figure 2. U.S. Army Force Projection Operations in 2023 Extend From Bringing Personnel to a State of Readiness for War to Their Eventual Redeployment to the Home Theater (Source: U.S. Army [18]).
Nifty Nugget was also the first exercise to thoroughly examine the World-Wide Military Command and Control System (WWMCCS), a computerized C2 system developed in the 1960s to coordinate and control operational activities along the entire chain of command. WWMCCS was found to not be able to “walk and chew gum at the same time” [19]. The system posted slow response times, could not keep up with Nifty Nugget’s computing tempo, and suffered from a lack of flexibility. Because its preset deployment orders were issued automatically, any change was likely to hamstring multiple units for days [19]. In one instance, an airlifting team “received 27 validated requests to move the same unit to 27 different places” [15].
Operation Desert Shield
The DoD took Nifty Nugget’s logistical failures to heart. The Joint Chiefs of Staff created a Joint Deployment Agency (JDA) soon thereafter and charged it with consolidating deployment tasks across the department [15, 18]. To underscore its authority to task units from other forces, the JDA was later elevated to combatant command status as the U.S. Transportation Command (USTRANSCOM). In 1990, its information-management capabilities played a critical role in executing Operation Desert Shield, the largest projection of expeditionary military force—by any nation—since the end of World War II [20].
In just over two months, USTRANSCOM oversaw the movement of more than 120,000 troops, 700 armored tanks, 1,400 fighting vehicles, and 600 artillery pieces into the seaports and deserts of Saudi Arabia [20]. With Iraqi forces unable to contest U.S. force projection tasks via stand-off attacks, American forces embarked for the Middle East by any means available to them, sometimes even via chartered commercial flights (see Figure 3). U.S. equipment and personnel were dispatched so rapidly—three times the rate achieved during the War in Vietnam [21]—that many soldiers arrived to find insufficient accommodations present in theater. Some even turned to sleeping in the open sand [20, 22].

Figure 3. U.S. Marines Board a Commercial Aircraft Chartered by U.S. Military Airlift Command at an Undisclosed Location During Operation Desert Shield, September 1990 (Source: DVIDS [23]).
Its hiccups notwithstanding, Operation Desert Shield was seen as a “spectacular” success, and USTRANSCOM’s synchronization of airlift, sealift, prepositioned stocks, and in-theater resources was hailed as a “logistical marvel” [15]. Central to this effort was the command’s computerized Joint Operation Planning and Execution System (JOPES), a subsystem of the WWMCCS, which had been developed specifically to solve the transportation C2 problems seen during CPX Nifty Nugget. However, at the outset of operations in 1990, many officers did not trust JOPES. It lacked in-transit visibility of cargo and passenger movements, and many senior commanders opted to bypass JOPES entirely. It was seen as a bureaucratic tool that had “no place in a real war” until a major on-the-fly software overhaul—and orders for stricter adherence to JOPES procedures—made it an essential part of Desert Shield’s logistical success [15].
The First Information War
It did not take the hindsight of history for the Persian Gulf War to become known as “the Computer War.” It was the first conflict determined by modern technology, and it became closely identified with American precision-guided munitions, night-vision goggles, and stealth aircraft [24]. However, many strategic analysts regarded the conflict as the first Information War, more attuned as they were to the contribution made by more mundane systems like the WWMCCS and JOPES. They recognized that for all her technological might, the American way of warfare relied far more heavily on logistical data and IT systems than it did on “smart” bombs or stealth [24, 25].
This reliance, however, was also recognized as a source of vulnerability. As one retired U.S. Air Force colonel opined in 1992, coalition forces had come to see information “as a utility; ubiquitous, commonly shared, commonly financed, uncommonly reliable, and always available or almost always…forgotten are those infrequent but terrifying moments when global finance or air traffic control networks are halted by momentary lapses in computer or human behavior” [25]. Adversarial militaries across the world took similar note. In direct response to the war’s outcome, the People’s Liberation Army (PLA) of the People’s Republic of China (PRC) began to aggressively expand its capabilities in technical reconnaissance, offensive cyberspace operations, and warfare in the electronic, psychological, communications, and information spaces [26, 27].
In 2015, the PLA established the Strategic Support Force (SSF) as a theater command-level organization to centralize its assets in “informationized” warfare. Current PLA information doctrine calls for it to wage warfare on an adversary’s morale, psychology, public opinion, legal structures, and media narratives to “disrupt [its] military operations”—especially during the initial stages of a conflict [27]. For adversarial nations, the ability of U.S. forces to deploy to the Persian Gulf freely was instructive. The conflict’s lesson for the PLA was the importance of significantly improving its counter-C2 and information warfare capabilities to disrupt hostile deployment actions that might target PLA forces.
Information Advantage in MDO
The MDO framework originated in the mid-2010s, the partial product of Commander Gen. David G. Perkins’s pushing for TRADOC to grapple with the growing threat from peer states in the cyber and space domains [28]. The 2018 National Defense Strategy’s pronouncements that the “homeland is no longer a sanctuary” and that the DoD must achieve “information superiority” over its adversaries codified the need to develop a new operational concept for the Army [28].
In its simplest form, MDO is built upon a fundamental recognition that cyber and information technologies made “traditional methods” of offensive action (in one or two domains) all but obsolete [10]. Adversary courses of action (COAs) will instead combine effects throughout the land, maritime, air, space, and cyberspace domains, as well as strike across the physical, information, and human dimensions of military action (see Figure 4). (Note that Joint and U.S. Army terminology for MDO and IA differs in places.) MDO functions as a type of prompt for commanders to fully understand and visualize the complexity of the modern operational environment relative to their position in it.
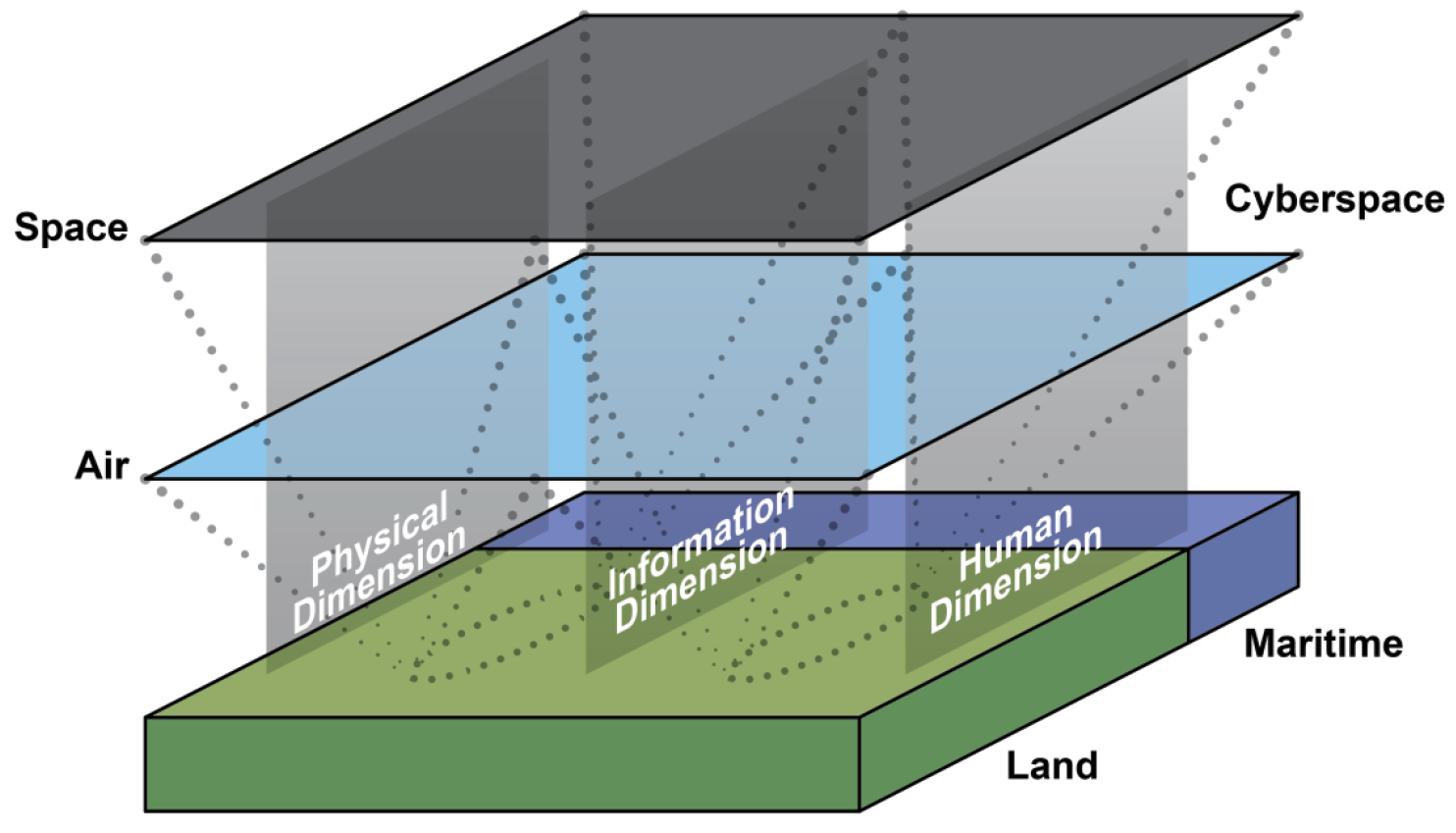 Figure 4. Domains and Dimensions of the MDO Operational Environment as Defined in U.S. Army Field Manual (FM) 3-0, Operations (Source: U.S. Army [10]).
Figure 4. Domains and Dimensions of the MDO Operational Environment as Defined in U.S. Army Field Manual (FM) 3-0, Operations (Source: U.S. Army [10]).
The Army’s conception of IA presented in ADP 3-13 is similarly positioned. Many of the technical tasks that fall within its scope pertain to the DoD’s equipment and systems: soldiers are to protect friendly data, information, and systems; counter adversarial efforts at electronic or cyber surveillance; and follow operational security practices to conceal friendly capabilities and intentions [7]. Even so, if ADP 3-13’s definition of information as “data in context to which a receiver assigns meaning” comes to find more widespread adoption than its doctrinal predecessors, it will be, in part, because it stresses the practical and subjective nature of the information dimension [4, 5]. As one student of doctrinal history explained, IA will go “to the side that possesses better information and uses that information more effectively” [4].
One underappreciated aspect of the Army’s information doctrine is recognizing that because ADP 3-13 is freely accessible online, the document may itself change what COAs in information warfare our adversaries may pursue. The PLA’s information warfare officers in the SSF have unquestionably studied ADP 3-13 and are monitoring how the Army plans to implement its guidance. The SSF has also studied another Army doctrinal publication, FM 3-0, Operations, and paid close attention to its guidance on how to “conduct deployment operations contested by a peer threat” [10]. Central to preserving IA during a contested deployment is maintaining awareness that, to a considerable extent, the chance of a surprise attack of a previously unknown nature approaches the inevitable [29].
Threat Courses of Action
In a fictionalized account written in 2021 for the U.S. Army Future Warfare Writing Program, Maj. Timothy M. Dwyer paints a truly chilling—and utterly plausible—tale. Soon, all the narrator’s electronic devices, systems, networks, and digital accounts have been penetrated by the PLA’s information forces [30]. On the morning he is to deploy to Hawaii, the internet-connected smart speaker in his daughter’s room intones that “your mommy, your daddy, your sister, they will all die.” After the soldier smashes it into oblivion, he finds that his home’s other smart devices have been capturing indecent photos of his family—now uploaded to their social media accounts. His personal vehicle will not start, and then the electricity to his home is turned off. “I could barely get out of my house,” the soldier recalls [30]. “Fat lot of good our carriers and tanks are when the fighting was all virtual.”
The initial threat from a peer state will come in the form of cyber-based attacks on critical infrastructure nodes in the homeland. Hostile actors will seek to incapacitate energy production networks, transportation, government administration, and other critical public services like water treatment systems [31]. Threat COAs will then use nonkinetic information attacks to disable DoD deployment systems like JOPES or the Defense Manpower Data Center and to delay or stop troop and materiel movements by disrupting key highways, bridges, and ports (see Figure 5) [32].
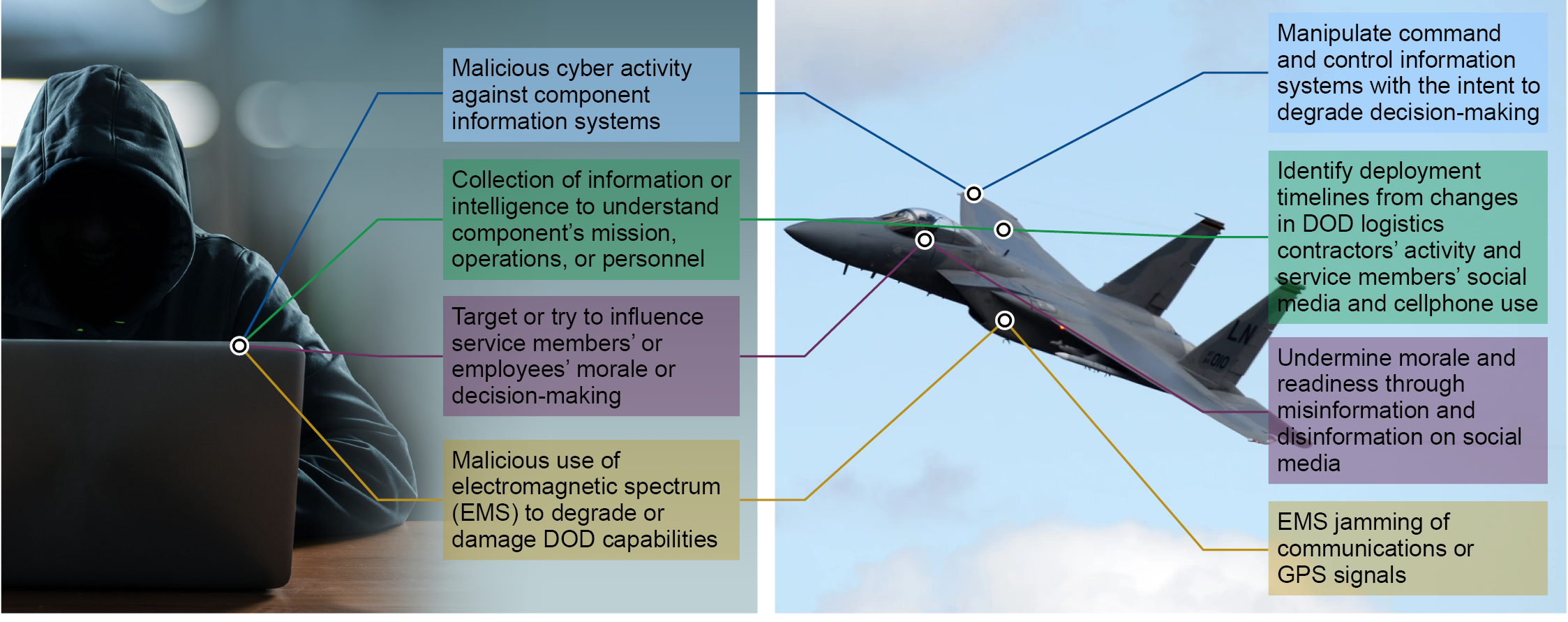 Figure 5. Example Threat Actions in the Information Dimensions (Source: GAO [33]).
Figure 5. Example Threat Actions in the Information Dimensions (Source: GAO [33]).
A peer threat may then turn to information warfare tactics to generate harmful cognitive effects in U.S. service members and the public at large [10]. Specifically, an information-capable adversary will (a) keep U.S. service members and units under constant reconnaissance, (b) seek to influence individual troops to preclude their mobilization, and (c) manipulate the public to possibly interfere with deployment operations.
Persistent Reconnaissance and Intelligence
Most adversarial efforts to contest a deployment will rely first on the ability to continuously fix and track U.S. forces. This is easier done than may be credibly imagined. Already, the battlefield has become “data-swept,” littered with billions of networked devices that continuously share information. Like the smart speaker of Maj. Dwyer’s story, such devices now create more cyberspace activity than people do directly; of that activity, an estimated 95+% of traffic remains unencrypted [34].
Writing in the Military Review in 2020, Army Cpt. T. S. Allen argues that we will soon “live in a world where most movement generates a cyberspace signature” [34]. The use of smartphones in Ukraine to record and share graphic clips of progress in combat is but one example of how media-enabled, open-source intelligence can be used to find and fix target locations and identify combatants [35]. More consequentially, as one DoD contractor recently demonstrated, capabilities currently exist to track smartphones in real time, without the aid of spyware, and to tie their data streams to discrete individuals even if anonymized. As a result, “smartphones can be repurposed as sensors without [the user] even being aware” [36].
The defense community has long recognized that U.S. military units generate a considerable degree of nonvisual signatures. While the use of the run-logging application Strava by troops in the Middle East in 2018 likely did not reveal any sensitive information about U.S. bases, it stands as a good reminder that American units are highly “trackable, traceable, and predictable” [37]. Similar geotagging practices were used in 2022 to trace the buildup of Russian infantry units prior to their ultimate invasion of Ukraine. Even if an American unit can shield themselves from any signature emissions during a deployment mission from fort to port, just the absence of the unit’s normal routine patterns of life around its home installation will alert adversaries to its intentions. As Cpt. Allen notes, “every ‘hidden’ action … sparks an easily monitored reaction” [34].
Direct Influence
Persistent surveillance enables another COA—directly influencing Warfighters to preclude them from reporting for duty. While Maj. Dwyer’s tale was fiction, his story has already found at least one analogue in the real world. During a 2019 NATO exercise, a “red team” of communications experts used open-source data to spoof the social media accounts of soldiers’ loved ones. They then “catfished” many into leaving their posts—all for the princely sum of about $60 [38]. Russian forces have used similar tactics for deadly effects in Ukraine [39]. In one scenario, the parents of a targeted soldier will receive a text message that their child is dead, prompting them to call. Thus shaken, the soldier receives a text imploring them to “retreat and live” by heading to a marked location. A deadly artillery strike soon follows.
The sources of soldier coercion may be as simple as the previous example or based on highly specific information. In 2023, Duke University researchers found that detailed personal data on thousands of active-duty U.S. troops were readily accessible through data brokers, some via commonplace .org or .asia domains. Health data, financial records, and even religious affiliations could be bought as cheaply as $0.12 per record [40]. Elsewhere, U.S. intelligence leaders have pointed to efforts by genomics institutes in the PRC to tap into DNA databases of U.S. citizens as a first step toward future coercion [37]. In late 2023, hacks of two high-profile, family-history, genetic testing firms sought to extract the identities of those with Ashkenazi Jewish and Chinese heritage, seeking an as-of-yet unknown but chilling advantage over them [41].
Elsewhere, multiple active-duty troops (and veterans) have been radicalized through online forums in recent years, with some of them suborned into firing upon their colleagues [42]. During the stress of an LSCO deployment, the risk of prior nonviolent but still latent radicalization resulting in a call to action—or simply of Warfighters falling prey to malign phishing attacks—will be acute [33]. Soldier ability to maintain the highest levels of cognitive understanding may also suffer (see Figure 6). In Maj. Dwyer’s story, he recounts a scene in which the narrator hears an unconfirmed radio report of the PLA sinking two American carrier strike groups (CSGs) near Guam. Properly incredulous at first, the narrator then hears the same news from his father via text message before seeing expertly simulated video footage of the carrier group’s destruction played on a major news outlet. His commander concludes that he “must assume that two CSGs were destroyed” [30].
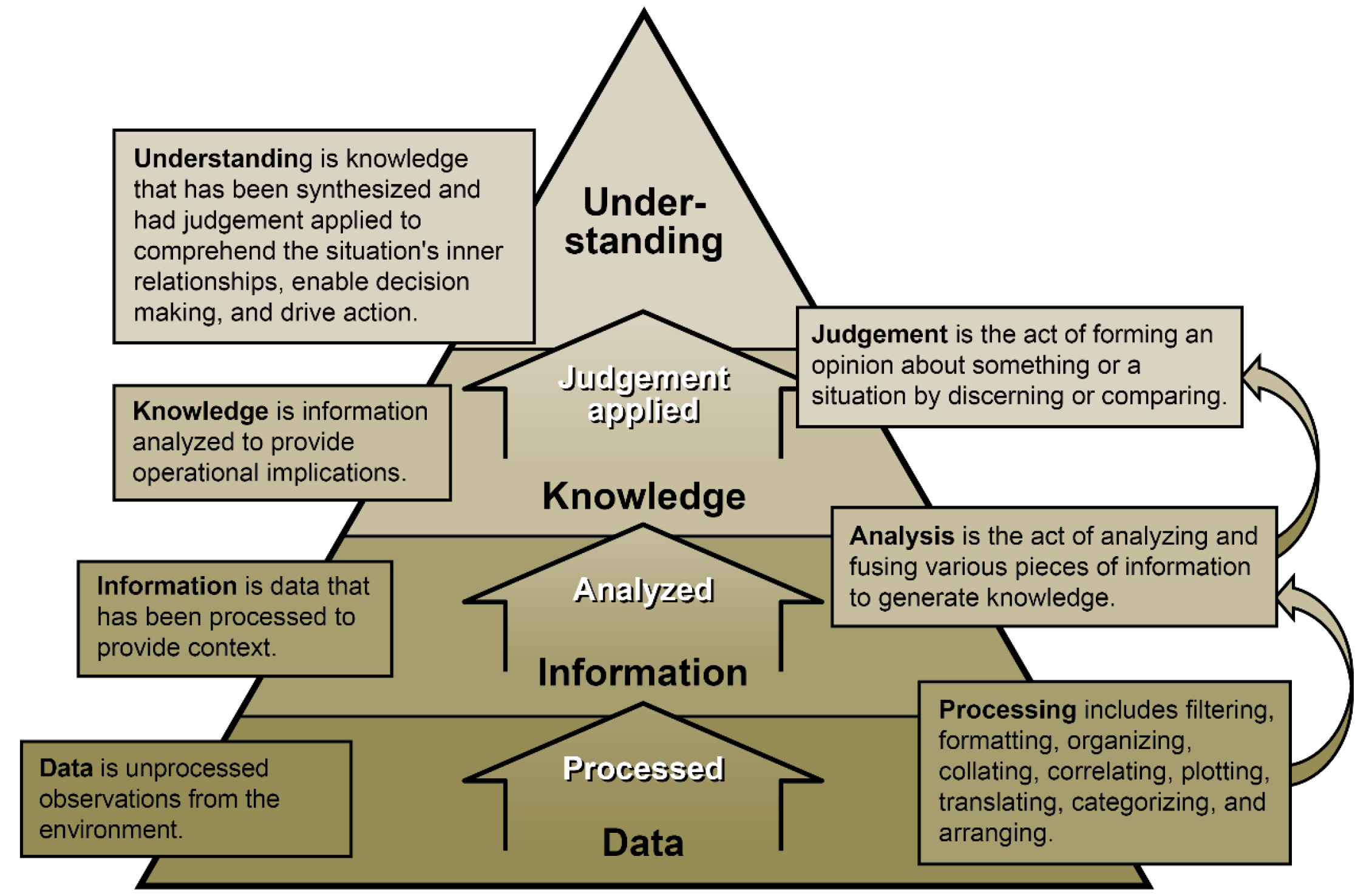
Figure 6. Cognitive Hierarchy: How Humans Progressively Assign Meaning to Data Into Understanding (Source: U.S. Army [7]).
Public Interference
As real-time information streams have come to dominate global media-content consumption, it has become commonplace to say that “contemporary wars are largely wars of influence” or ones fought by narratives [43]. Russian disinformation campaigns are produced for dissemination in large volumes and often push grand, overarching stories to gradually influence public opinion [44]. Indeed, this has already been done to great effect, stretching over decades of time. In the 1970s and 1980s, a Russian disinformation campaign effectively spread whispers that the HIV/AIDS epidemic was the secret product of U.S. government biological research [45]. The distrust in public health officials caused by this still lingers today.
As social media-based information warfare matures, however, an aperture has opened for adversaries to deploy targeted, specific influence campaigns to achieve near-term objectives. Indeed, the PLA’s SSF believes that warfare in the cognitive dimension is most effective when “telling partial truths” and in small doses [46]. Doing so helps recruit the widest possible range of adherents and may better spur them to action.
An emerging concern stems from as-of-yet-unclear future uses of artificial intelligence (AI). In 2019, the PLA added the AI-enabled “intelligentized” warfare to its already-robust informationized warfare capabilities [47]. The widespread use by young Americans of the Chinese-owned mobile phone app TikTok (now notorious for its rapid spread of propaganda), combined with the propensity of existing chat-based, generative-AI, large language models to report false statements, has created an exceptionally large information space for public manipulation [48].
The opportunities for turning public opinion against U.S. deployment operations will scale with the size of the expeditionary force mobilized. Threat COAs may inflame antiwar sentiments among local groups and push them to rush military convoys in transit or to occupy naval vessels or airframes set to embark. Indeed, a group of protestors in November 2023 achieved just such an aim, albeit for only a few hours [49]. They blocked the Ready Reserve Force supply ship MV Cape Orlando from departing Oakland before they were arrested and perimeter control was restored (note that there is no known evidence of foreign interference or influence upon the group).
Some aspects of the DoD’s force projection architecture are particularly vulnerable to this type of event. For instance, a scholar at the Brookings Institution estimated in 2013 that nearly 50% of military cargo needed in the early stages of an overseas contingency operation would flow through a single point—the Port of Beaumont [32]. Outside of targeting military installations directly, peer adversaries are likely to stage small, irregular attacks at major public events like a Major League Baseball game or the Indianapolis 500 to tie up countless law enforcement and National Guard assets and further hinder the normal flow of traffic and commerce.
Conclusions
Improved technology can certainly help the DoD protect its forces and the American public from malign narratives from adversarial threats. The Army Research Office is already funding advanced research into applying high-speed computational servers to the task of processing large volumes of multimodal online media content in real time to quickly identify and combat coordinated cognitive attacks like those envisioned by the PLA [50].
However, IA’s emphasis on the value of turning data, information, and knowledge into understanding is a strong hint toward another solution set. The risk of overreliance on big data analytics may be to downplay critical thought, adaptive expertise, and creativity in warfare to predict or perceive that the threat is being fully tracked and managed [51]. At a minimum, U.S. Warfighters might first dust off their analog tools of yore and refamiliarize themselves to the chalkboards, printed maps, and spoken-word orders that currently remain unhackable [52]. For the central virtue of IA rests not in the digital realm but in the soldier—its critical tasks are “seeing yourself” and understanding the operational environment “while denying the same to your adversary” [53].
References
- Stapleton, R. A. “Three Perspectives on the Information Technologies and National Security: War Fighting, Diplomacy and Intelligence.” Computer Professionals for Social Responsibility, http://cpsr.org/prevsite/conferences/cfp93/stapleton.html, June 1993.
- Warriner, A. “The Pizza Meter.” http://home.xnet.com/~warinner/pizzacites.html, 1997.
- Miller, M. “What Can Pizza Tell Us About Ourselves?” Slate, https://slate.com/human-interest/2016/07/the-pizza-meter-was-a-staple-of-1990s-pop-pseudoscience-we-should-revive-it.html?pay=1701964280669&support_journalism=please, 29 July 2016.
- White, S. P. “The Organizational Determinants of Military Doctrine: A History of Army Information Operations.” Texas National Security Review, vol. 6, no. 1, pp. 51–78, http://dx.doi.org/10.26153/tsw/44440, Winter 2022–2023.
- Ross, R. J. “Information Advantage Activities: A Concept for the Application of Capabilities and Operational Art During Multi-Domain Operations.” Cyber Defense Review, https://cyberdefensereview.army.mil/Portals/6/Documents/2021_fall/06_Ross_CDR_V6N4-Fall_2021.pdf?ver=aj3AhXhZLEGojxeZ2Gb42A%3d%3d, Fall 2021.
- Harper, J. “Pentagon Unveils New Strategy for Operating in the Information Environment.” DefenseScoop, https://defensescoop.com/2023/11/17/pentagon-unveils-new-strategy-for-operating-in-the-information-environment/, 17 November 2023.
- U.S. Army. Information. ADP 3-13, Washington, D.C.: Headquarters, Department of the Army, https://armypubs.army.mil/epubs/DR_pubs/DR_a/ARN39736-ADP_3-13-000-WEB-1.pdf, November 2023.
- U.S. DoD. 2022 National Defense Strategy of the United States of America. https://media.defense.gov/2022/Oct/27/2003103845/-1/-1/1/2022-NATIONAL-DEFENSE-STRATEGY-NPR-MDR.PDF, 27 October 2022.
- U.S. Department of the Navy. The Department of the Navy Cyber Strategy. https://media.defense.gov/2023/Nov/21/2003345095/-1/-1/0/DEPARTMENT%20OF%20THE%20NAVY%20CYBER%20STRATEGY.PDF, 21 November 2023.
- U.S. Army. Operations. FM 3-0, Washington, D.C.: Headquarters, Department of the Army, https://armypubs.army.mil/ProductMaps/PubForm/Details.aspx?PUB_ID=1025593, 1 October 2022.
- Gamble, D. A. “Driving Modernization, Maintaining Readiness: Aligning Sustainment’s Role and Efforts in the Push to 2035.” Army Sustainment, PB 700-21-03, Headquarters, Department of the Army, pp. 6–7, https://alu.army.mil/alog/ARCHIVE/PB7002103FULL.pdf, July–September 2021.
- Kretchik, W. E. U.S. Army Doctrine: From the American Revolution to the War on Terror. Lawrence: University Press of Kansas, 2011.
- Ancker, C. J. “The Evolution of Mission Command in U.S. Army Doctrine, 1905 to the Present.” Military Review, Fort Leavenworth, KS: Army University Press, pp. 42–52, https://usacac.army.mil/sites/default/files/documents/mccoe/TheEvolutionOfMissionCommandInArmyDoctrine.pdf, March–April 2013.
- Endress, C. A. “Mobilization (Historical Bibliography No. 7).” Fort Leavenworth, KS: pU.S. Army Command and General Staff College, https://www.armyupress.army.mil/Portals/7/combat-studies-institute/csi-books/endress.pdf, 1987.
- Matthews, J. K., and C. J. Holt. So Many, So Much, So Far, So Fast: United States Transportation Command and Strategic Deployment for Operation Desert Shield/Desert Storm. Joint History Office, Office of the Chairman of the Joint Chiefs of Staff, and Research Center, U.S. Transportation Command, https://apps.dtic.mil/sti/pdfs/ADA323609.pdf, 1996.
- Canan, J. W. “Up From Nifty Nugget.” Air & Space Forces Magazine, https://www.airandspaceforces.com/article/0983nifty/, 1 September 1983.
- Getler, M. “Make-Believe Mobilization Showed Major Flaws.” The Washington Post, https://www.washingtonpost.com/archive/politics/1980/07/24/make-believe-mobilization-showed-major-flaws/e6d0c81b-22a3-4ac0-9b46-2e334d5d3f70/, 24 July 1980.
- U.S. Army. “Army Deployment and Redeployment Processes and Procedures.” Pamphlet 525–93, Washington, D.C.: Headquarters, Department of the Army, https://armypubs.army.mil/epubs/DR_pubs/DR_a/ARN34280-PAM_525-93-000-WEB-1.pdf, 6 October 2023.
- Pearson, D. E. The World Wide Military Command and Control System: Evolution and Effectiveness. Maxwell Air Force Base, AL: Air University Press, https://apps.dtic.mil/sti/pdfs/ADA379709.pdf, June 2000.
- U.S. Army Center of Military History. War in the Persian Gulf: Operations Desert Shield and Desert Storm, CMH Pub 70-117-1, Washington, D.C., https://history.army.mil/html/books/070/70-117-1/CMH_70-117-1.pdf, 2010.
- Isreal, E. M. “Operational Logistics During the First Gulf War.” Fort Leavenworth, KS: School of Advanced Military Studies, U.S. Army Command and General Staff College, https://apps.dtic.mil/sti/trecms/pdf/AD1159141.pdf, May 2020.
- Kindsvatter, P. S. “VII Corps in the Gulf War: Deployment and Preparation for Desert Storm.” Military Review, Army University Press, pp. 1–16, https://www.armyupress.army.mil/Portals/7/PDF-UA-docs/Kindsvatter-UA.pdf, January 1992.
- Air Mobility Command Public Affairs. “20 Years After Operations Desert Shield, Desert Storm: Airlift Effort Was Compared to ‘Moving a Small City’ [Image 2 of 3].” DVIDS: Defense Visual Information Distribution Service, Photo ID 900901-F-AB111-001, https://www.dvidshub.net/image/376190/20-years-after-operations-desert-shield-desert-storm-airlift-effort-compared-moving-small-city, 1 September 1990.
- Mansky, J. “Operation Desert Storm Was Not Won By Smart Weaponry Alone.” Smithsonian Magazine, https://www.smithsonianmag.com/history/operation-desert-storm-was-not-won-smart-weaponry-alone-180957879/, 20 January 2016.
- Reardon, T. M. “Information Warfare: Protecting Force Sustainment.” Military Intelligence Professional Bulletin. U.S. Army Intelligence Center of Excellence, https://irp.fas.org/agency/army/mipb/1997-1/reardon.htm, January–March 1997.
- Dahm, M. “China’s Desert Storm Education.” Proceedings, vol. 147/3/1,417, U.S. Naval Institute, https://www.usni.org/magazines/proceedings/2021/march/chinas-desert-storm-education#:~:text=PLA%20lessons%20learned%20from%20the%20Gulf%20War%20led,war%20that%20drives%20PLA%20force%20structure%20and%20strategy, March 2021.
- U.S. DoD. 2023 Military and Security Developments Involving the People’s Republic of China: Annual Report to Congress. Washington, D.C., https://media.defense.gov/2023/Oct/19/2003323409/-1/-1/1/2023-MILITARY-AND-SECURITY-DEVELOPMENTS-INVOLVING-THE-PEOPLES-REPUBLIC-OF-CHINA.PDF, November 2023.
- Fawcett, G. S. History of US Army Operating Concepts and Implications for Multi-Domain Operations.” Fort Leavenworth, KS: School of Advanced Military Studies, U.S. Army Command and General Staff College, https://apps.dtic.mil/sti/pdfs/AD1083313.pdf, 2019.
- Horner, C. A. “What We Should Have Learned in Desert Storm, But Didn’t.” Air & Space Forces Magazine, https://www.airandspaceforces.com/article/1296horner/, 1 December 1996.
- Dwyer, T. M. “The American Maginot Line.” Fort Leavenworth, KS: Army University Press, Military Review, https://www.armyupress.army.mil/Journals/Military-Review/English-Edition-Archives/September-October-2021/Dwyer-American-Maginot-Line/, September–October 2021.
- U.S. Army. “The Operational Environment and the Changing Character of Warfare (TRADOC Pamphlet 525-92).” Fort Eustis, VA: Training and Doctrine Command, https://adminpubs.tradoc.army.mil/pamphlets/TP525-92.pdf, 7 October 2019.
- Tussing, B. B., J. E. Powell, and B. C. Leitzel. Contested Deployment. Carlisle, PA: Strategic Studies Institute, U.S. Army War College Press, U.S. Army War College, https://press.armywarcollege.edu/cgi/viewcontent.cgi?article=1944&context=monographs, 2022.
- U.S. Government Accountability Office. “Information Environment: Opportunities and Threats to DOD’s National Security Mission.” GAO-22-104714, https://www.gao.gov/assets/gao-22-104714.pdf, September 2022.
- Allen, T. S. “Finding the Enemy on the Data-Swept Battlefield of 2035.” Military Review, https://www.armyupress.army.mil/Journals/Military-Review/English-Edition-Archives/November-December-2020/Allen-Data-Swept-2035/#:~:text=On%20the%20data%2Dswept%20battlefield%2C%20the%20armed%20force%20best%20postured,to%20win%20in%20these%20conditions, November–December 2020.
- Perrigo, B. “How Open Source Intelligence Became the World’s Window Into the Ukraine Invasion.” Time, https://time.com/6150884/ukraine-russia-attack-open-source-intelligence, 24 February 2022.
- Ford, M. “Ukraine, Participation and the Smartphone at War.” Political Anthropological Research on International Social Sciences, vol. 4, no. 2, pp. 219–247, https://brill.com/view/journals/pari/4/2/article-p219_005.xml, December 2023.
- Smith, M., and N. Starck. “Open-Source Data Is Everywhere—Except the Army’s Concept of Information Advantage.” Modern War Institute at West Point, https://mwi.westpoint.edu/open-source-data-is-everywhere-except-the-armys-concept-of-information-advantage, 24 May 2022.
- Pickrell, R. “NATO Troops Were Located, Tricked Into Disobeying Orders in Research Experiment.” Military.com, https://www.military.com/daily-news/2019/02/20/nato-troops-were-located-tricked-disobeying-orders-research-experiment.html, 20 February 2019.
- Collins, L. “Russia Gives Lessons in Electronic Warfare.” Association of the United States Army, https://www.ausa.org/articles/russia-gives-lessons-electronic-warfare, 26 July 2018.
- Sherman, J., H. Barton, A. Klein, B. Kruse, and A. Srinivasan. “Data Brokers and the Sale of Data on U.S. Military Personnel: Risks to Privacy, Safety, and National Security.” Sanford School of Public Policy, Duke University, https://techpolicy.sanford.duke.edu/wp-content/uploads/sites/4/2023/11/Sherman-et-al-2023-Data-Brokers-and-the-Sale-of-Data-on-US-Military-Personnel.pdf, November 2023.
- Katersky, A. “Connecticut Attorney General Presses 23andMe for Data Breach Answers.” ABC News, https://abcnews.go.com/US/connecticut-attorney-general-presses-23andme-data-breach-answers/story?id=104510476, 31 October 2023.
- Posard, M. N., L. A. Payne, and L. L. Miller. “Reducing the Risk of Extremist Activity in the U.S. Military.” PE-A1447-1, RAND Corporation, https://doi.org/10.7249/PEA1447-1, September 2021.
- Maan, A. “Narrative Warfare.” Weaponized Narrative Initiative, Arizona State University, https://weaponizednarrative.asu.edu/publications/narrative-warfare, 3 April 2018.
- OECD. “Disinformation and Russia’s War of Aggression Against Ukraine: Threats and Governance Responses.” https://www.oecd.org/ukraine-hub/policy-responses/disinformation-and-russia-s-war-of-aggression-against-ukraine-37186bde/#boxsection-d1e348, 3 November 2022.
- Kramer, M. “Lessons From Operation ‘Denver,’ the KGB’s Massive AIDS Disinformation Campaign.” The MIT Press Reader, https://thereader.mitpress.mit.edu/operation-denver-kgb-aids-disinformation-campaign/, May 2020.
- Davis, C. “Cognitive Warfare: China’s Effort to Ensure Information Advantage.” Military Intelligence, https://mipb.army.mil/articles/jul-dec-2023/cognitive-warfare, July–December 2023.
- Takagi, K. “The Future of China’s Cognitive Warfare: Lessons from the War in Ukraine.” War on the Rocks, https://warontherocks.com/2022/07/the-future-of-chinas-cognitive-warfare-lessons-from-the-war-in-ukraine, 22 July 2022.
- Tucker, P. “How Often Does ChatGPT Push Misinformation?” DefenseOne, https://www.defenseone.com/technology/2024/01/new-paper-shows-generative-ai-its-present-formcan-push-misinformation/393128/?oref=d1-skybox-hp, 4 January 2024.
- Castaneda, C. “Pro-Palestinian Protesters Delay Military Supply Ship From Departing Port of Oakland.” CBS San Francisco, https://www.cbsnews.com/sanfrancisco/news/pro-palestinian-protesters-block-military-supply-ship-at-the-port-of-oakland, 3 November 2023.
- Talk Business & Politics. “UA Little Rock Receives $5 Million From U.S. Army to Study Information Campaigns.” https://talkbusiness.net/2023/11/ua-little-rock-receives-5-million-from-u-s-army-to-study-information-campaigns, 27 November 2023.
- Ross, C. “The Unknowable Future of Warfare.” The Strategy Bridge, https://thestrategybridge.org/the-bridge/2023/3/20/the-unknowable-future-of-warfare, 30 March 2023.
- Nelson, C., and A. Rhodes. “Embrace Analog Tools in a Digital Intelligence Age.” Proceedings, vol. 146/10/1,412, U.S. Naval Institute, https://www.usni.org/magazines/proceedings/2020/october/embrace-analog-tools-digital-intelligence-age, October 2020.
- Myatt, S. “Impending TRADOC Document Outlines Pathway for Army to Achieve Information Advantage; Lt. Gen. Maria Barrett Quoted.” GovConWire, https://www.govconwire.com/2022/07/arcyber-document-explores-army-information-advantage, 13 July 2022.
Biography
Joel Hewett is an energy policy and national defense researcher, writer, and analyst for KeyLogic, where he applies more than 15 years of experience in assessing the utility of advancements in science and technology. In his role, he supports multiple federal agencies in studies addressing energy systems and critical infrastructure protection issues. Among his published works is a state-of-the-art report for the Homeland Defense & Security Information Analysis Center on military microgrids, “Resilience by Design: Microgrid Solutions for Installation Energy.” Mr. Hewett holds an M.S. from the Georgia Institute of Technology in the history and sociology of technology and science and an A.B. in literature from Davidson College.