Introduction
The internet of things (IoT) is a growing network of billions of connected devices. In 2015, approximately 15.4 billion devices were part of the IoT, and current research indicates 30.7 billion devices partaking in the network by 2020 [1]. The IoT is now part of the every day, integrated into homes by way of cameras and door locks and into infrastructure through Cyber-Physical Systems (CPS),
such as the smart grid and the Internet of Battlefield Things (IoBT). The IoT provides the framework for internet-connected CPS, which are closely integrated, context-aware, mission-critical systems that perform actions and interact with the physical world (see Figure 1) [2-4]. CPS are evolving and expanding with many applications still in research and development stages.
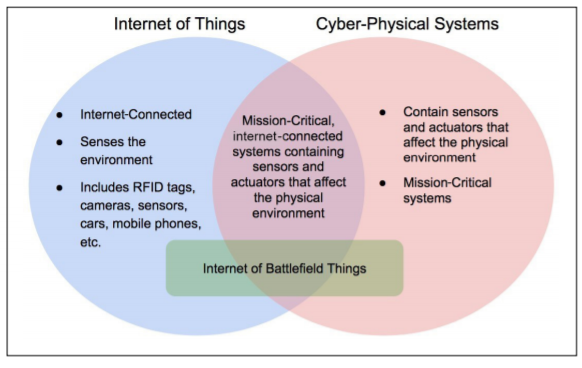
Figure 1: IoT and CPS intersection with IoBT
Smart systems (platforms such as CPS that incorporate IoT) have become an important component of infrastructure, particularly those aspects regulated, maintained, and utilized by federal agencies. The adoption of the IoT within the federal government has been largely driven by the Department of Defense (DoD), the Department of Homeland Security, and the National Aeronautics and Space Administration [5]. The expansion of smart systems has affected operations within DoD so much that the Defense Information Systems Agency, which is essentially DoD’s information technology combat support agency, has acknowledged the urgent need to keep demands related to this shift at the forefront of defense architecture [6]. In general, the impact of the IoT has garnered the attention of DoD leadership prompting the release of policy recommendations for the IoT in 2016 [7]. As smart systems, particularly CPS, become more widespread, it is necessary to adopt a standard framework for their integration into existing aspects of infrastructure [8]. When considering the implementation of IoT/CPS into infrastructure, security is a primary concern.
All IoT/CPS systems require the devices in the system be able to securely communicate (even though that communication will often conform to a sparse interconnection topology). In IoT/CPS systems, there are two primary categories of devices: edge devices and gateways. Edge devices are limited resource devices containing sensors and actuators. The edge devices collect and transmit data to the gateway(s) or perform actions requested by the gateway(s). The gateway device is responsible for collecting and aggregating data from edge devices, providing directives for the edge devices, connecting the edge devices to the internet (or intranet), and transmitting data to a cloud or private data store.
Cyber Security Challenges
Many cyber security challenges exist for the IoT, CPS, and IoBT. Networking of these devices is accomplished via multiple protocols, such as radio-frequency identification, Wi-Fi, and Bluetooth – among others. Furthermore, the devices composing the IoT/CPS incorporate a variety of hardware
specifications and chipsets. Proper implementation of standard security measures is made more difficult by the inherent abundance of factors that must be considered within a network composed primarily of IoT/ CPS devices.
Additionally, the mobility of IoT/CPS devices raises a unique set of security concerns. Devices not bound to fixed locations (whose distance between other devices and access points is not constant) will have variable connectivity. Additional security concerns that must be accounted for include lost data packets
and unattended devices that may become compromised. In systems composed of distributed devices, communication between the devices is pivotal for facilitating the proper function of the system. A lack
of resiliency is an inability to identify and adapt to the presence of nodes within the system that exhibit weak or outright negative performance, which can cripple the utility provided by the system. Finally, the resource constraints that IoT/ CPS devices face must be taken into consideration. Redundancy and encryption would at least mitigate, and could solve, some of the aforementioned problems, but the devices within these systems must be strategic in the functions on which they choose to expend energy. Thus, it is critically important for less resource-heavy security methods to be strategically evaluated and implemented.
Trust Management Systems for Internet of Things/Cyber-Physical Systems
Trust management systems (TMS) are used to establish trust between two entities and are used in many areas of computing including peer-to-peer networks [9,10], wireless sensor networks [11,12], and, more recently, IoT systems [13-15]. The TMS must be adaptable for a wide range of scenarios and applications.
Trust propagation is the method in which peers propagate evidence to one another in a centralized or distributed fashion. In the proposed approach, trust propagation will occur in a hybrid fashion wherein devices propagate information to each other as well as a central trust data store when they are able. The centralized data store enables devices to move throughout the system while maintaining a certain level
of trust. This can keep a malicious device from corrupting one part of the system, being blacklisted from that section, and moving to a new section to cause corruptions. The central data store would provide the information allowing that section of the system to know the device is blacklisted. Distributed trust management is ideal for the IoT and allows the system to compute scores for only small subsets of known neighbors, which are devices within direct communication based on being within one hop of communication. The calculation of the trust scores is accomplished through trust aggregation (the method by which the data will be aggregated for trust score calculations) by fuzzy sets, game theory, and Bayesian analysis [16,17]. Fuzzy logic uses if-then rule sets to solve the trust problem and provide a multi-logic value [17]. Bayesian trust models use Bayes’ theorem as a foundation for aggregation and have been widely used and implemented over the last decade. They are studied in wireless sensor networks, peer-to-peer networks applications, and IoT systems [17-20]. Game theory models compute a trust score using minimal resources, which is an advantage in limited-resource devices, such as IoT edge
devices [21]. Unlike Bayesian trust models and fuzzy logic trust models, game theory models don’t predict what will occur. Instead, they mathematically estimate the behavior of the participants [17].
Trust composition will include direct and indirect observations, such as the success of packet transmissions and performing an action. Direct observations will have the most impact in calculating the trust of another device. However, the indirect observations are important to provide a balance and better understanding of the true nature of a device. The observations are taken on a range of [0,1], where 0 indicates the device did not perform some particular action and 1 indicating the device perfectly
performed that action. This allows for fractional outcomes. A device could receive a 0.75 rating for an action, meaning it was successful in performing the action but not 100 percent. An average of all direct observations OD is taken, and the incremental average of indirect observations OI for device n for the ith observation is sent (ODi) using the incremental average such that
![]()
The same can be done for indirect observation OI as they are propagated. This is used when calculating the probability of success for a device’s reputation through data aggregation.
To aggregate the data to calculate a trust score, a dual approach with Bayesian and game theory is advantageous. Game theory provides a lightweight method for edge devices to determine trust through a trust matrix, whereas Bayesian analysis provides a more in-depth trust score calculation that can occur in a gateway and be propagated to the edge device when necessary. Bayesian analysis attempts to predict the probability of a device performing a desired action given the device’s previous actions. The previous actions are both the direct and indirect observations that are propagated through firsthand experience and by the neighbors. The probability that a device D will successfully complete tasks is calculated using Bayes Theory such that
![]()
In this particular case, Pr(S) = 1 since success is expected. For Pr(D|S), this probability is identified based on direct and indirect observations. Indirect observations can be weighted by a factor of ω, such that
![]()
Given this, the probability of D is all observations of the data such that
![]()
To generalize, the trust score TS for device n is
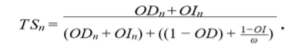
Figure 2 illustrates the lifecycle events of TMS for a device. It shows a device D1 entering into a new system and connecting to a gateway. D1 can be either an edge device or gateway device entering the system. The following steps occur for D1 as the device learns about neighboring devices and maintains status within the system.
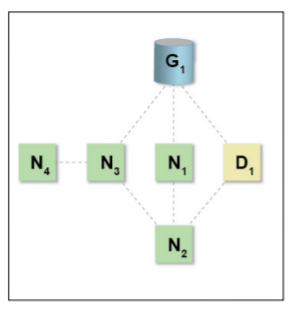
Figure 2: Device Entry into TMS
- Device D1 enters the system and is given a neutral trust score with the
gateway G1 and with device neighbors N1 and N2. - D1 performs actions as requested by G1, N1, and N2.
- With each request, G1, N1, and N2 update their trust of D1.
- Periodically, G1, N1, and N2 share their trust score of D1 with each other, and G1 will share the scores with the central data store.
- The process maintains as long as D1 is in the system.
- If D1 moves throughout the system and belongs to a new gateway, G2, the central data store can be reached, if available, to set an initial score for D1 that is a more accurate level of trust than the initial neutral trust score.
- If the device trust score ever drops below a desired threshold, the device can be quarantined until further intervention occurs (such as a higher-level algorithm, system administrator/operator review, or an offline forensic test).
This system provides a mechanism for monitoring devices while they are in use. Through this implementation, misbehaving devices may be detected, both malicious and faulty, and alert the system administrator of the problem.
Use Cases
As IoT/CPS systems become more prevalent, they are also beginning to have an impact on the battlefield – referred to as the IoBT [22]. Figure 1 shows the attributes and intersection of IoT and CPS and how the
IoBT incorporates qualities from both. The IoBT is the collection of devices that can be attached to vehicles or worn by soldiers in the battlefield, such as drones, sensors, and cameras. These devices must maintain secure communication in order to effectively work. If the devices are continuously moving throughout the system, it’s imperative they maintain authentication into the system and continuous correct functionality.
Implementation of a TMS would enable these devices to maintain a trust score as they are used in the system. To accommodate mobility (and in some cases the transient nature) of these devices, a central data store can provide the means for a device to maintain its trust as it moves around. This provides a framework to keep malfunctioning and malicious devices from corrupting the entire system. If a device is blacklisted in one section of the system, it can’t move to a new section to cause corruptions because the trust score propagates. The TMS provides a reliable means of monitoring devices as well
as activity associated with these IoBT-enabled devices used by warfighters moving throughout the system. Earlier this year, the U.S. Army Research Laboratory established a Collaborative Research Alliance to address challenges in IoBT including heterogeneity, connectivity, scalability, and interdependence of networked elements [23]. Another major area of research in CPS is the smart grid. The smart grid is the use of cutting-edge technologies, equipment, and operations to make the delivery of electricity more reliable and efficient [24] than legacy systems. The Department of Energy defines seven key requirements for a smart grid: self-healing, motivates and includes the consumer, resists attacks, provides power quality, accommodates generation and storage options, enables markets, and optimizes assets for efficient operation [25,26]. The goal of the smart grid is to provide an infrastructure capable of handling distributed generation, renewable energy sources, electric vehicles, and demand-side management electricity [25]. As these technologies work together to control the delivery of electricity, it’s imperative they maintain acceptable performance. A TMS can be used to evaluate whether each device in the system is reliable for performing its designated task. Furthermore, a TMS can
revoke privileges to any device that becomes unreliable or faulty. The aforementioned TMS incorporates both dimensions of faultiness and potential cyber threat.
Conclusions and Further Explorations
IoT and CPS are quickly becoming integrated into civil infrastructure and the battlefield. ATMS provides a key mechanism for establishing, maintaining, and revoking trust of devices within IoT/CPS systems. This provides a foundation to establish a more secure and resilient system by blacklisting devices not
performing desired actions. It is imperative that such functionality exist in the context of highly mobile devices that would otherwise be capable of compromising multiple parts of a system. On-going research is needed to continue development of TMS for IoT/CPS with the aim of strengthening the speed at which
misbehaving devices are detected and improving the ability to identify malicious versus
faulty devices.
References
1. Columbus, L. (2016, November). Roundup of internet of things forecasts and market estimates. Forbes. Retrieved from https://www. forbes.com/sites/louiscolumbus/2016/11/27/ roundup-of-internet-of-things-forecasts-andmarket-estimates-2016/#4d5e1228292d (accessed July 19, 2017)
2. Banerjee, A., Venkatasubramanian, K. K., Mukherjee, T., & Gupta, S. K. (2012). Ensuring safety, security, and sustainability of mission-critical cyber-physical systems. Proceedings of the IEEE, 100(1), 283-299. doi:10.1109/jproc.2011.2165689
3. Shi, J., Wan, J., Yan, H., & Suo, H. (2011). A survey of cyber-physical systems. In
2011 International Conference on Wireless Communications and Signal Processing (WCSP) (pp. 1-6). IEEE. doi:10.1109/ WCSP.2011.6096958
4. Baheti, R., & Gill, H. (2011). Cyber-physical systems. In The Impact of Control Technology (pp. 161-166). IEEE Control Systems Society. Retrieved from http://ieeecss.org/general/impact-control-technology (accessed July 19, 2017)
5. Goldstein, P. (2016, June 10). DOD, DHS and NASA are driving adoption of internet
of things sensors. FedTech Magazine. Retrieved from https://fedtechmagazine.com/article/2016/06/dod-dhs-and-nasa-are-driving-adoption-internet-things-sensors (accessed July 19, 2017)
6. Defense Information Systems Agency. (2015). DISA Strategic Plan 2015-2020. Retrieved from http://www.disa.mil/~/media/files/disa/about/strategic-plan.pdf (accessed July 19, 2017)
7. Department of Defense. (2016). DoD Policy Recommendations for the Internet of Things
(IoT). Department of Defense, Office of the Chief Information Officer. Retrieved from https://www.hsdl.org/?abstract&did=799676 (accessed July 19, 2017)
8. National Institute of Standards and Technology. (2013). Foundations for Innovation in Cyber-Physical Systems (Workshop Report). Retrieved from https://www.nist.gov/ sites/default/files/documents/el/CPS-WorkshopReport-1-30-13-Final.pdf (accessed July 19, 2017)
9. Kamvar, S. D., Schlosser, M. T., & Garcia-Molina, H. (2003). The Eigentrust algorithm for reputation management in P2P networks. In Proceedings of the 12th International Conference on World Wide Web,
WWW 2003 (pp. 640-651). New York, NY: ACM. doi:10.1145/775152.775242
10. Xiong, L., & Liu, L. (2004). PeerTrust: Supporting reputation-based trust for peerto-peer electronic communities. IEEE Transactions on Knowledge and Data Engineering, 16(7), 843-857. doi:10.1109/
tkde.2004.1318566
11. Jadidoleslamy, H., Aref, M. R., & Bahramgiri, H. (2016). A fuzzy fully distributed trust management system in wireless sensor networks. International Journal of Electronics and Communications, 70(1), 40-49. doi:10.1016/j.aeue.2015.09.017
12. Ganeriwal, S., & Srivastava, M. B. (2004). Reputation-based framework for high integrity sensor networks. In Proceedings of the 2nd ACM workshop on Security of ad hoc and sensor networks (pp. 66-77). New York, NY: ACM. doi:10.1145/1029102.1029115
13. Chen, I., Guo, J., & Bao, F. (2016). Trust management for SOA-based IoT and its application to service composition. IEEE Transactions on Services Computing, 9(3), 482-495. doi:10.1109/tsc.2014.2365797
14. Mendoza, C. V., & Kleinschmidt, J. H. (2016). Defense for selective attacks in the IoT with a distributed trust management scheme. 2016 IEEE International Symposium on Consumer Electronics (ISCE), 53-54. doi:10.1109/isce.2016.7797367
15. Dorodchi, M., Abedi, M., & Cukic, B. (2016). Trust-based development framework for distributed systems and IoT. 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), 437-442. doi:10.1109/compsac.2016.21318.
16. Jøsang, A., Ismail, R., & Boyd, C. (2007). A survey of trust and reputation systems for online service provision. Decision Support Systems, 43(2), 618-644. doi:10.1016/j. dss.2005.05.019
17. Yu, Y., Li, K., Zhou, W., & Li, P. (2012). Trust mechanisms in wireless sensor networks: Attack analysis and countermeasures. Journal of Network and Computer Applications, 35(3), 867-880. doi:10.1016/j. jnca.2011.03.005
18. Han, G., Jiang, J., Shu, L., Niu, J., & Chao, H. (2014). Management and applications of trust in Wireless Sensor Networks: A survey. Journal of Computer and System Sciences, 80(3), 602-617. doi:10.1016/j. jcss.2013.06.014
19. Guo, J., Chen, I., & Tsai, J. J. (2017). A survey of trust computation models for service management in internet of things systems. Computer Communications, 97, 1-14. doi:10.1016/j.comcom.2016.10.012
20. Thirunarayan, K., Anantharam, P., Henson, C., & Sheth, A. (2014). Comparative trust
management with applications: Bayesian approaches emphasis. Future Generation Computer Systems, 31, 182-199. doi:10.1016/j.future.2013.05.006
21. Mehdi, M. M., Raza, I., & Hussain, S. A. (2017). A game theory based trust model for Vehicular Ad hoc Networks (VANETs). Computer Networks, 121, 152-172. doi:10.1016/j. comnet.2017.04.024
22. U.S. Army Research Laboratory. (n.d.) Internet of battlefield things (IOBT). Retrieved from https://www.arl.army.mil/www/default. cfm?page=3050 (accessed July 19, 2017)
23. Blinde, L. (2017, March 6). ARL launches Internet of Battlefield Things CRA. Retrieved from http://intelligencecommunitynews.com/ arl-launches-internet-of-battlefield-thingscra/ (accessed July 19, 2017)
24. U.S. Department of Energy. (n.d.). Grid modernization and the smart grid. Retrieved from https://energy.gov/oe/services/technology-development/smart-grid (accessed June 29, 2017)
25. Sridhar, S., Hahn, A., & Govindarasu, M. (2012). Cyber–physical system security for the electric power grid. Proceedings of the IEEE, 100(1), 210-224. doi:10.1109/ jproc.2011.2165269
26. National Energy Technology Laboratory. (2007). A systems view of the modern grid (Rep. for the U.S. Department of Energy Office of Electricity Delivery and Energy Reliability).


